Given the frequent appearance of fresh cyber-attacks in media reports, now is an opportune moment to assess the vulnerability of your owned devices and explore optimal strategies for safeguarding them against diverse forms of cyber threats.
What constitutes a Botnet Army?
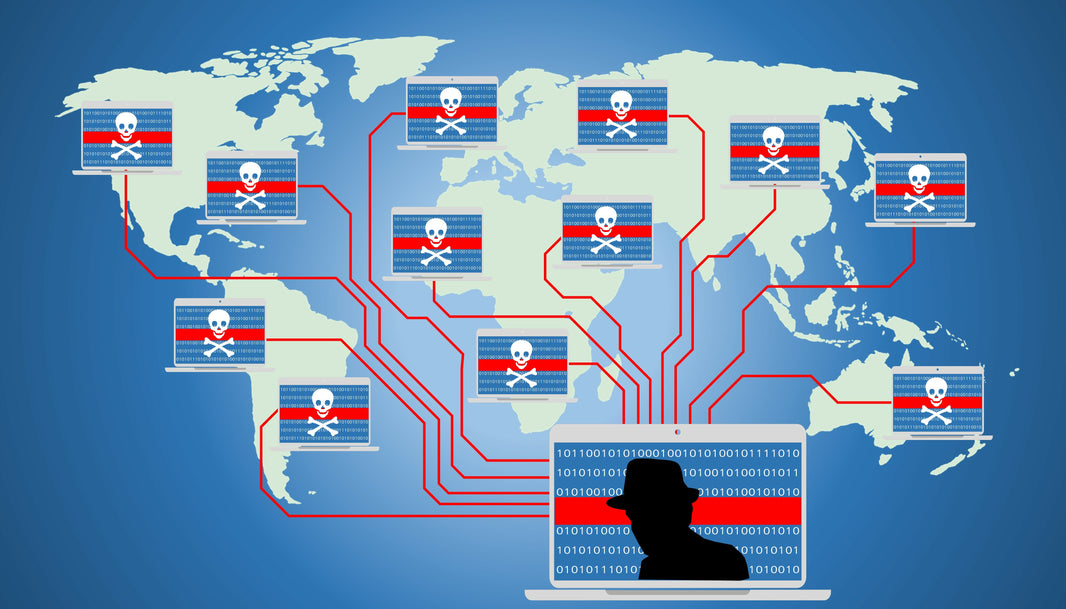
A Botnet Army comprises a collection of interlinked bot devices tainted with malware and orchestrated by a lone assailant or entity.
These bots encompass a variety of gadgets found within the Internet of Things (IoT) realm, spanning sensors, computers, and beyond.
Botnet engagement in IoT has surged 35% over the past year, underscoring the escalating risk.
What objectives drive a Botnet Army?
The primary aim of a botnet army is to harness a large array of compromised devices to execute malicious operations worldwide.
By infecting home routers and IoT devices with detrimental malware, these malevolent entities establish networks of infected devices for future assaults.
Cybercriminals utilize these botnets to launch diverse cyberattacks, including the notorious distributed denial-of-service (DDoS) attacks.
During a DDoS onslaught, numerous PCs inundate a domain with packets to disrupt connectivity, wreaking havoc for internet service providers and cybersecurity experts endeavoring to counteract it.
Botnet armies also serve to orchestrate social media campaigns, forge anonymous proxy networks, mine private data, and more.
How are Botnet Armies Recognized?
One of the foremost challenges in combatting botnet armies lies in the modular nature of the malware, enabling it to adeptly adapt and encrypt its communication with command and control servers.
This poses a formidable obstacle for cybersecurity professionals striving to detect and mitigate these threats effectively.
Fortunately, numerous cybersecurity experts worldwide devote themselves to monitoring and scrutinizing traffic clusters, enabling them to flag and investigate any suspicious communications among devices.
How can a Botnet Army Infiltrate my Network?
Cybercriminals and other malicious entities capitalize on privacy vulnerabilities and potential security flaws in internet-connected devices to infect them with harmful malware.
An emerging trend among botnet armies is to target end-of-life routers and IoT devices lacking robust security protocols compared to newer models, which factor in the escalating prevalence of such attacks.
Your devices may encounter the infectious malware through various means, with the most common being having a publicly visible IP address while browsing online.
These malware infestations can linger undetected for extended periods, posing a latent threat to end-users.
Concealing your genuine IP address with a VPN service constitutes one of the most effective measures to safeguard your device's IP address from detection and targeting in an attack.
Fortunately, Rio's cutting-edge router boasts a built-in VPN, ensuring the comprehensive encryption of the identity, location, and communication of all your linked devices. Moreover, Rio's sophisticated security measures and intrusion prevention mechanism safeguard against botnet attacks, fortified by its zero trust security posture. With Rio, solely authorized devices gain entry to your network, necessitating your approval before accessing it.
What is TheMoon Botnet Army?
Initially identified in 2014, TheMoon Botnet Army was believed to be dormant until recently discovered by Black Lotus Labs. This latest iteration, part of a lengthy malware campaign, has expanded significantly in scope.
Comprising over 40,000 bots across 88 countries, TheMoon continues to proliferate rapidly. Its method involves infecting home routers and IoT devices, empowering it to establish an expansive network of bots fueling an anonymous proxy service called FaceLess.
How does TheMoon Differ from Other Botnets?
TheMoon distinguishes itself with a novel objective, gaining traction among cybercriminals. Rather than executing DDoS attacks or data mining, it redirects infected devices to an Anonymous Proxy Service known as Faceless.
Faceless, favored by cybercriminals, encrypts and reroutes internet traffic, complicating law enforcement efforts to trace activity. By harnessing numerous malware-infected devices globally, FaceLess users achieve online anonymity as their activities appear to originate from these compromised devices.
Which Devices are Most Vulnerable to Botnet Cyber Attacks?
The current trajectory of TheMoon and FaceLess indicates a preference for older, end-of-life home routers and IoT devices. Wi-Fi 5 or earlier routers are particularly susceptible, suggesting an urgent need for upgrades.
The advent of Wi-Fi 6, Wi-Fi 6E, and Wi-Fi 7 introduces new security protocols to bolster network and data protection. Given that compromised credentials jeopardize entire networks, safeguarding all connected devices, including those used by family members, is paramount.
With every Rio router, users gain access to a suite of advanced security features. This includes dual-level password protection and SecureRoom technology, which acts as a safeguard by isolating approved devices into their own dedicated rooms. Within these rooms, communication is restricted solely to devices within that specific enclave, effectively preventing any potentially compromised devices from spreading their influence to other devices on the network. Moreover, SecureRoom adds an extra layer of defense by requiring additional passwords, further fortifying against the risks posed by compromised credentials.
Can a VPN Shield Me from a Botnet Cyber Assault?
Employing security measures like utilizing a VPN is an effective strategy to safeguard against botnet armies. However, given the continuous emergence of security vulnerabilities in connected devices, the battle against botnet armies persists.
Opting for Rio, with its built-in VPN capability and additional enterprise-grade security features, presents another effective method to counter recent botnet cyber onslaughts, particularly those targeting outdated router models nearing the end of their lifecycle.
What Constitutes an Intrusion Prevention System?
An Intrusion Prevention System (IPS) is a security tool meticulously crafted to shield a network or system from malicious attack traffic and unforeseen disruptions.
By employing diverse techniques such as default deny/allowlisting, machine learning, simulation, and authentication, an IPS is adept at identifying and thwarting an extensive array of threats, encompassing botnet infections and denial of service attacks.
How Does an Intrusion Prevention System Safeguard My Network?
Intrusion Prevention Systems serve as a formidable defense for numerous internet of things (IoT) devices with considerable exposure to the external environment, effectively curtailing online crime or data breaches that may compromise personal information.
By vigilantly monitoring the network and scrutinizing potential attack vectors, an IPS effectively minimizes the attack surface and prevents unauthorized nodes from infiltrating the network.
Operating in conjunction with an intrusion detection system (IDS), an IPS promptly identifies and mitigates incoming threats. Leveraging a set of performance metrics, the system discerns between normal and malicious behavior, leveraging machine learning techniques to continually enhance its detection capabilities.
What Are the Advantages of a VPN Router with Intrusion Prevention?
The distinctive advantage of a VPN Router with Intrusion Prevention, such as Rio, lies in its capability to swiftly analyze and block incoming threats in real-time.
This capability is especially critical in today’s digital landscape, where cybercriminals frequently deploy new malware to exploit vulnerabilities in connected devices. Harnessing the power of artificial intelligence and machine learning algorithms, the router adeptly detects and prevents unauthorized access to networks.
Given the proliferation of IoT devices in both residential and commercial settings, safeguarding sensitive data has become paramount.
A VPN router equipped with intrusion prevention like Rio offers a decentralized approach to security, furnishing a comprehensive protection layer for all connected devices. By actively monitoring network traffic, the router effectively thwarts intrusions before they can inflict harm.
The user-friendly plug-and-play setups render implementation of security measures effortless, even for individuals lacking expertise in cybersecurity. Moreover, the router’s real-time threat detection and prevention capabilities are invaluable in today’s dynamic threat landscape.
Whether it's an unsuspecting Reddit user downloading new malware or a malicious actor attempting to infiltrate the network, a VPN router with intrusion prevention like Rio offers peace of mind.
Leveraging state-of-the-art technologies, these routers remain ahead of hackers’ tactics, effectively countering threats ranging from botnet-based assaults targeting specific websites to sophisticated IoT botnets orchestrating massive DDoS attacks.